Nmap, short for Network Mapper, is a powerful open-source tool widely used for network discovery and security auditing. Whether you are a network administrator, a security professional, or a tech enthusiast, understanding nmap can significantly enhance your ability to analyze and secure your systems. Its essential features, including host discovery, port scanning, and service detection, make it a go-to utility for identifying devices on a network and assessing their security posture.
In this blog post, we will explore nmap from the ground up. We will guide you through the installation process on various operating systems, ensuring you're equipped to get nmap up and running smoothly. Additionally, we will delve into common scanning techniques and practical use cases, providing you with the skills to effectively use nmap in real-world scenarios. By the end of this post, you'll have a solid foundation in nmap that will empower you to take control of your network's security.
Introduction to nmap and its essential features
Nmap, or Network Mapper, is a powerful open-source tool widely used for network discovery and security auditing. It enables users to discover hosts and services on a computer network, thereby creating a detailed map of the network structure. With its versatile capabilities, Nmap can effectively identify open ports, running services, and the operating systems of devices within a network. This valuable information helps system administrators and security professionals identify potential vulnerabilities, assess network security, and troubleshoot connectivity issues.
One of Nmap's standout features is its ability to perform different types of scans, including TCP SYN scan, UDP scan, and service version detection. Each scanning technique serves a specific purpose, allowing users to gather precise details with minimal effort. Additionally, Nmap offers scripting capabilities through Nmap Scripting Engine (NSE), which enables users to automate various tasks and extend the tool's functionalities. By mastering Nmap's essential features, users can enhance their understanding of network environments and improve their overall security posture.
How to install nmap on various operating systems
Installing nmap is a straightforward process that varies slightly depending on your operating system. For users on Windows, the easiest way to install nmap is by downloading the installer from the official nmap website. Simply navigate to the download page, choose the Windows installer, and run the executable. Follow the on-screen instructions, and you’ll have nmap ready for use within minutes. Additionally, you can also use package managers like Chocolatey, which allows you to install nmap with a simple command: choco install nmap. This method is particularly useful for users who prefer command-line tools.
On macOS, nmap can be installed using the Homebrew package manager. If you haven't already installed Homebrew, you can do so by pasting the command provided on the Homebrew website into your terminal. Once you have Homebrew set up, installing nmap is as easy as typing brew install nmap in your terminal. For Linux users, most distributions include nmap in their package repositories, making it accessible through standard package managers. For instance, on Ubuntu, you can install nmap by executing sudo apt-get install nmap. In Fedora, you would use sudo dnf install nmap. These installation methods ensure that you can quickly get started with nmap, regardless of your operating system.
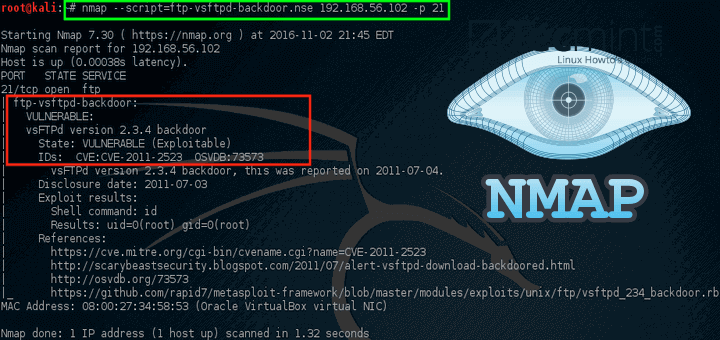
Common nmap scanning techniques and use cases
Nmap offers a variety of scanning techniques that cater to different needs and scenarios. The most common methods include TCP connect scans, SYN scans, and UDP scans. TCP connect scans establish a full connection with the target, making it simple but easily detectable by firewalls. On the other hand, SYN scans send only SYN packets, allowing users to identify open ports without completing the handshake process, making it stealthier. For those who need to assess services running on specific ports, Nmap's version detection feature can provide essential details about the software and its version, enabling system administrators to identify vulnerabilities and ensure compliance with security standards.
In addition to these fundamental techniques, Nmap excels in its versatility across various use cases. Security professionals frequently use Nmap to perform network reconnaissance and vulnerability assessments. By identifying active hosts and open ports, they gain critical insights into the security posture of a network. System administrators also leverage Nmap for routine tasks, such as monitoring network performance and troubleshooting issues. Furthermore, penetration testers utilize advanced features like script scanning to automate the detection of weaknesses in services, significantly enhancing their testing efficiency. Whether you're a novice exploring the world of network security or a seasoned professional, mastering Nmap’s scanning techniques can elevate your cybersecurity efforts.